What is NTP?
NTP uses the concept of a stratum to describe how many NTP hops away a machine is from an authoritative time source, usually a reference clock. A reference clock is a stratum 0 device that is assumed to be accurate and has little or no delay associated with it. Stratum 0 servers cannot be used on the network but they are directly connected to computers which then operate as stratum-1 servers. A stratum 1 time server acts as a primary network time standard.
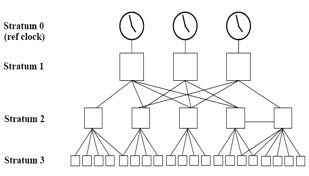
A stratum 2 server is connected to the stratum 1 server; then a stratum 3 server is connected to the stratum 2 server and so on. A stratum 2 server gets its time via NTP packet requests from a stratum 1 server. A stratum 3 server gets its time via NTP packet requests from a stratum-2 server… A stratum server may also peer with other stratum servers at the same level to provide more stable and robust time for all devices in the peer group (for example a stratum 2 server can peer with other stratum 2 servers).
. NTP is designed to synchronize the time on a network. NTP runs over the User Datagram Protocol (UDP), using port 123 as both the source and destination.
. To configure a Cisco device as an Authoritative NTP Server, use the ntp master [stratum] command. An Authoritative NTP Server can distribute time even when it is not synchronized to an existing time server.
. To configure the local device to use a remote NTP clock source, use the command ntp server <IP address>. For example: Router(config)#ntp server 192.168.1.1
. The ntp authenticate command is used to enable the NTP authentication feature (NTP authentication is disabled by default).
. The ntp trusted-key command specifies one or more keys that a time source must provide in its NTP packets in order for the device to synchronize to it. This command provides protection against accidentally synchronizing the device to a time source that is not trusted.
. The ntp authentication-key defines the authentication keys. The device does not synchronize to a time source unless the source has one of these authentication keys and the key number is specified by the ntp trusted-key number command.
. Two most popular commands to display time sources statistics: show ntp status and show ntp associations

Comments
Post a Comment